<center>
</center>
<br/>
Now in the past series I have talked about how to protect yourself against Kernel based threats, but there is one more thing or strategy that can be done, so this post will also be a [ring 0](https://en.wikipedia.org/wiki/Protection_ring) topic.
**Here are the episodes so far:**
* **1) [Hardware Selection & Proper Usage](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-1)**
* **2) [Hardware Selection & Proper Usage](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-2)**
* **3) [Kernel Defense](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-3)**
<BR/>
--------------------------
<br/>
# [Virtual Machine](https://en.wikipedia.org/wiki/Virtual_machine)
So in the past episode I have just described how people should use Linux, why to use Linux, and why should they update their OS constantly to the latest stable version. Basically keeping the kernel, above all, always updated.
However that does minimize the risk on the kernel side, since bugs are fixed pretty quickly, that is all that can be done on that side. But we can do things on the other side that we do have manual control over, basically setting up our entire computing setup in a way to minimize the risk even further.
* One method is [ASLR](https://en.wikipedia.org/wiki/Address_space_layout_randomization) which is mostly pre-configured and enabled in the boot menu, if not then you must enable it
* The other one is to just run everything inside a Virtual Machine
A virtual machine is like a box that traps all software and applications that runs inside it. So the kernel runs outside it, while all softwares gain like an additional “firewall” between it and the kernel, that can filter, block or route all commands, even the malicious ones.
<BR/>
### VM Strategy
Well the best strategy would be to just run everything inside a VM, so only the maintenance system is outside it, and everything else is inside it. So you will update the main kernel and the outside operating system, carefully, and never install any additional software in that space.
Instead everything will run inside the VM. Now this will take more resources, so not recommended for low end computers.
<CENTER>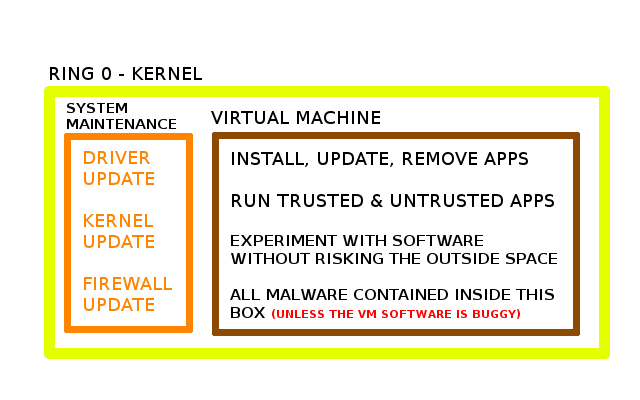</CENTER>
So this means that all apps trusted and untrusted will run inside the box, and hopefully nothing will escape. There is always a slight chance that stuff might escape, but it does lower it, so updating the VM software is also a priority.
And outside the box is just the basic maintenance, so the Main OS will be used just for that:
* Update & Configure the Kernel
* Update & Configure the VM software
* Update & Configure the Firewall
* Update & Configure the Drivers
And that’s it nothing more, any other use of the Main OS would risk the entire setup, so all other operations will be done inside the VM.
<BR/>
### VM Software
Now for the Main OS, you actually don’t need anything fancy since it will be just used for basic stuff, so choose a lightweight OS if you want to go with this strategy.
* [Lubuntu](https://en.wikipedia.org/wiki/Lubuntu) is an excellent OS as the “exo-skeleton”, it will be used just for maintenance.
* The VM software, most commonly used is [VirtualBox](https://en.wikipedia.org/wiki/VirtualBox), very easy to use and setup, and open source
* And the inside OS will be [Linux Mint](https://en.wikipedia.org/wiki/Linux_Mint) or whatever you want, fully loaded with all the apps you need
So installed and configure Lubuntu, setup the firewall, update it to latest version, install VirtualBox, and then install Linux Mint inside a Virtual Box partition, and then just run applications through that.
It sounds complicated but it’s actually very simple and it can be setup in 20-30 minutes.
<center>
<sup>By Boudhayan Gupta at en.wikipedia [GFDL](http://www.gnu.org/copyleft/fdl.html), [CC BY-SA 4.0 to 1.0](https://creativecommons.org/licenses/by-sa/4.0-3.0-2.5-2.0-1.0) or [GPL](http://www.gnu.org/licenses/gpl.html), from Wikimedia Commons</sup>
</center>
Now of course the main point of the VM is to isolate bad stuff from good stuff, so you’ll actually need multiple VM partitions, one for trustworty computing (financial/cryptocurrency stuff) and one for casual browsing (porn, “questionable websites” or websites full of ads that you might think are spreading malware).
**So the actual setup would be like this:**
<center>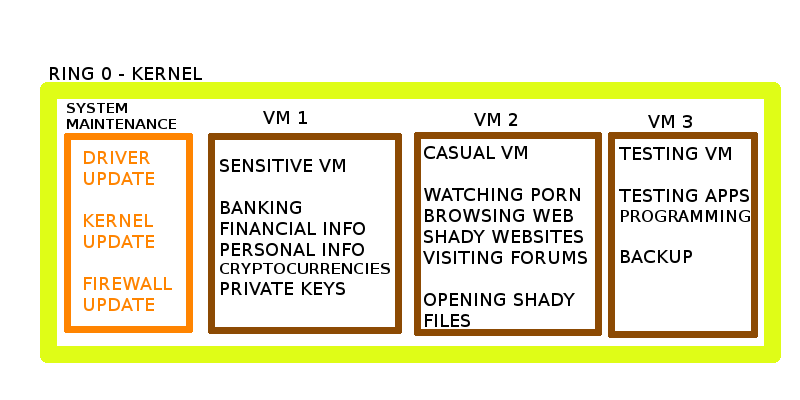</center>
So it’s compartimentalization, different things should be isolated, especially the potentially bad stuff from the sensitive stuff. And of course you don’t have to run all VM’s at the same time, only 1 at a time, otherwise it will be very resource intensive, since the OS inside the VM is an entire OS requiring the same amount of resources as if it were your Main OS.
A virtual machine can be thrown away like a used tampon, so whenever you feel the VM has been compromized, you just throw it away and create a new one. As long as the malware/exploit doesn’t escape the VM, the Kernel is safe.
So if you want to watch some porn or open untrustworthy .PDF files full of malware, then just use a dedicated VM for that, and throw it away after done.
<center><sup>By Zippie666 at nl.wikibooks (Own work - Linux) [GPL](http://www.gnu.org/licenses/gpl.html), from Wikimedia Commons</sup></center>
Basically a VM system is just a file of the size of the inside OS’s space. So the minimum I think is like 8 GB, so basically from the outside it’s just like a compressed file, and in the inside there is an entire operating system that you install.
So it would be a good idea to just install Linux Mint or whatever you choose 1 times and then copy paste that VM file (perhaps folder since I think it’s 2 files actually) as many times as you want. So just keep 1 folder as a template. And whenever you want a new one you just delete the used VM and create a new VM from the template.
So it is not just useful but even encouraged to throw away the VM as frequently as comfortable, since the system might get compromized periodically, it’s just inevitable especially if you are browsing the internet heavily, there might be some javascript malware that will compromize the system eventually.
Of course you will need to back your stuff up from there, if you don’t want it to be lost after you delete the VM, I will get into this immediately.
But first you also need to understand that the VM is just a shield for the Main OS, however if the sensitive VM gets compromized then it’s game over. So the sensitive VM containing the banking and cryptocurrency stuff should be taken care of to the highest degree. But I think even this should be thrown away periodically since it might get infected after a while (low probability if you are careful but still not impossible), and if the virus gets in but it doesn’t have access to the system yet since it’s waiting for another exploit, well in this case, regenerating the VM completely (perhaps with an updated OS) will both eliminate the virus and the potential future vulnerability that it could exploit to get activated.
So rotating the VM’s periodically is an excellent defense against dormant viruses. You never know what kind of app had what kind of vulnerability. Especially the browser, since that is the biggest attack vector, so even with best security practices, something can get through, but not activated yet until another stuff gets through too, sort of like a 2 step activation malware that is waiting for 2 applications to be vulnerable. Well in this case especially it’s advantageous to regenerate the VM, it wipes out both possibilities.
Now this has to be done carefully, and all personal data has to be backed up, but it’s hard to do!
<BR/>
### Moving Data out of the VM & Backup
So if you want to backup your work, which you should periodically (since the VM can get perhaps corrupted, so back up data frequently), but backing up data especially before destroying the VM.
Now this would mean that you would move data out of the VM into the Ring 0 environment, the Main OS, temporarily, which is really hard to do, I mean that is the whole point for everything to remain isolated.
Or it can be written to a CD or DVD from inside the VM. Sure a USB stick can be used too, but [USB sticks can carry malware as well](https://www.wired.com/2014/10/code-published-for-unfixable-usb-attack/).
So I’d just write the data to a CD/DVD from inside the VM, delete the VM, regenerate the VM from the template, and then copy back into the new VM from the CD/DVD. I think this is the safest way to do it, and it won’t touch the Main OS.
<BR/>
### Firewall
Last but not least the Main OS will be really the gateway between your secure setup and the internet. Everything will still be routed through it, especially the internet connections. So if the Main OS is compromized, then everything is compromized, so all of it has to be setup from the beginning.
So some of the risk is already lowered with the VM setup, malicious apps, unknown files, and things like that are isolated inside.
But the biggest attack vector is the internet itself, and while Linux is strong and transparent, a sophisticated hacker could attack the computer directly. So the Main OS has to be defended.
So defending against outside threats is just as important as defending against inside threats that can go out. This is why a powerful firewall has to be setup in the Ring 0 space on the external Main OS.
In Linux the main GUI firewall (since it’s mostly console based) is called [gufw](http://gufw.org/):
* If you don’t have it installed already just install `sudo apt-get install gufw`
<center>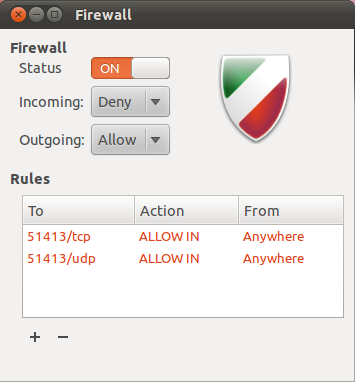</center>
Then start the firewall software and make sure you `disable incoming connections`. This is very important, otherwise hackers from outside could potentially DDOS your computer or even hack into it.
It’s a very usefriendly software, so you will figure it out. You can also block ports and IP addresses of suspicious origin, like known IP addresses of scammers in Bitcoin for example, and things like that.
So in the end your final setup would look like this:
<CENTER>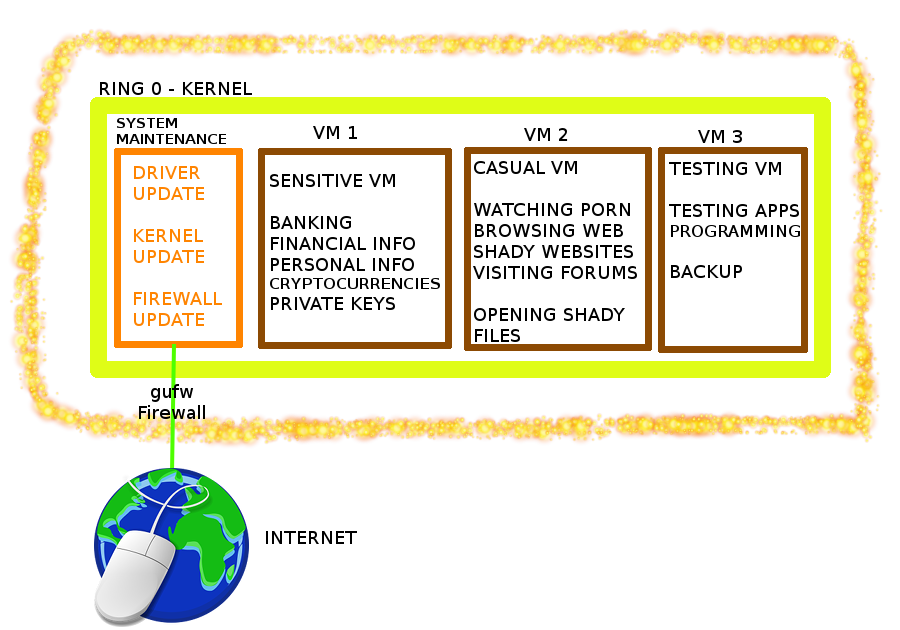</CENTER>
<BR/>
-----------------
<br/>
<CENTER></CENTER>
# Recap
**So let’s recap what you need to do:**
* Install a lightweight Linux Distribution ([Lubuntu](https://en.wikipedia.org/wiki/Lubuntu) or others) as your Main OS, which would only serve for maintenance purposes, so it must only have the bare minimum apps on it, both for security reasons and in order to not consume many resources since the VM will eat a lot.
* Configure the Main OS for maximum security, like installing a Firewall and configuring it, and always keeping it updated, furthermore not running any applications in this space to minimize the risk of it getting exposed to malware (since if the Main OS is compromized, the entire setup is compromized)
* Install a VM software, like [VirtualBox](https://www.virtualbox.org/)
* Install your preferred Linux Distribution like Linux Mint on a template VM
* Copy the template VM as many times as you like but don’t modify it since it will serve as a template to restore it in it’s original state
* Use the other copies of the VM for the roles specified above, but keep sensitive and casual activity separated between separate VM’s
* Whenever one VM is compromized, just backup the data from it, delete it, restore the VM from a template, and copy back the data to the fresh VM
* The template VM should be updated eventually as well to keep the pace with the updates and bug fixes.
------------------------------------------
**Sources:**
* https://pixabay.com
* Gufw screenshot, http://gufw.tuxfamily.org, [GPL](http://www.gnu.org/licenses/gpl.html), via Wikimedia Commons
-------------------------------------------
<CENTER><H1>Upvote, ReSteem & <a href="https://steemit.com/@profitgenerator" target='_blank'><img src='https://s4.postimg.org/cfz9b1mnh/bluebutton.png' border='0' alt='bluebutton'/></a></H1>
</CENTER>